A hacker group has released what it says is part of a 50-gigabyte haul of documents captured from Iran’s secretive nuclear programme.
The group had earlier set a 24-hour deadline for the Islamic regime to release protesters and political prisoners being held after arrests at anti-hijab demonstrations.
And when their demands were not met, the Black Reward hacktivists began releasing the data online.
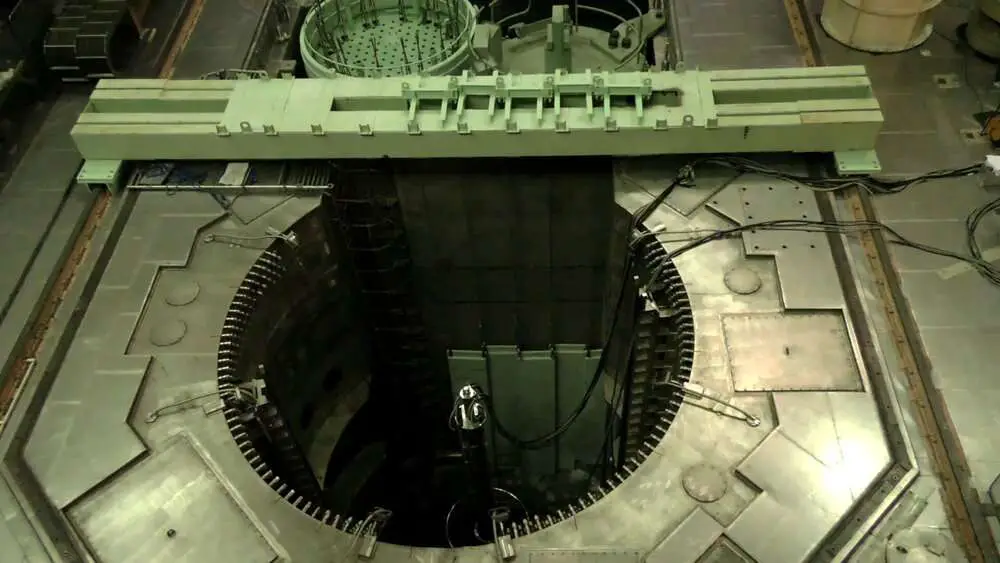
The video footage is part of the data released and it allegedly shows the inside of a nuclear power plant in Iran.
Only weeks ago Iran’s Supreme Leader Ayatollah Ali Khamenei’s senior adviser Kamal Kharrazi boasted how the state is now technically capable of making a nuclear bomb.
Thanks to its nuclear power stations, he bragged, Iran is ready to produce 90 per cent enriched uranium.
The hackers had announced on Friday that they had breached the email system of Iran’s Nuclear Power Production And Development Company and they threatened to release the documents they had obtained if the government did not stop clamping down on protesters.
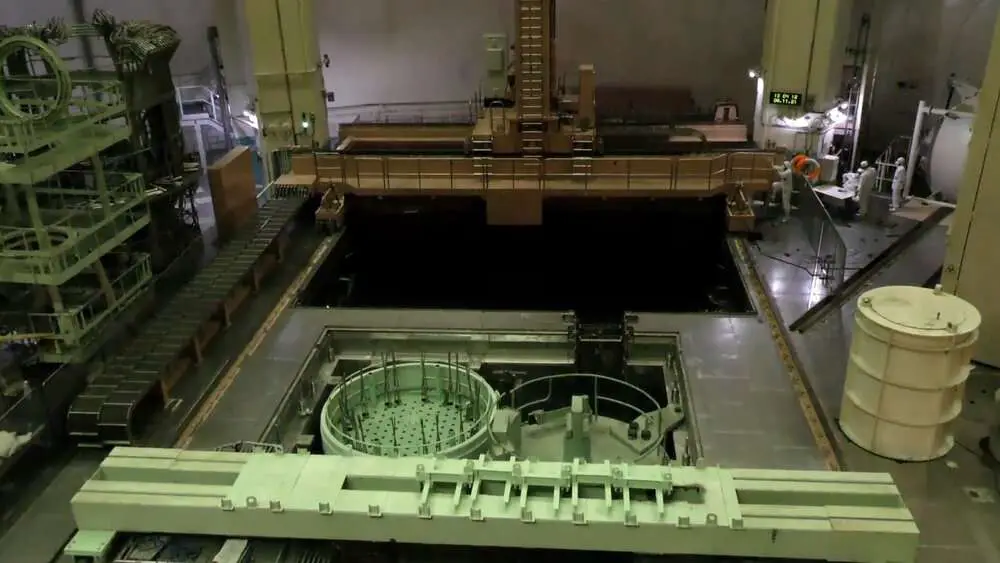
They gave the government 24 hours to comply before releasing some of the data they said they had obtained.
Independent Iranian media – including the London-based Iran International – reported Black Reward had said on Telegram: “The published documents contain the contracts of Iran Atomic Energy Production and Development Company with domestic and foreign partners, management and operational schedules of Bushehr power plant, identity details and paystub of engineers and employees of the company as well as passports and visas of Iranian and Russian specialists of Bushehr power plant.”
And in a scathing dig at Western governments, they added: “Unlike Westerners, we do not flirt with criminal clerics, and if we promise something, we fulfil it 100 per cent.”
The 11-second piece of footage appears to show the inside of an Iranian nuclear power plant, although Newsflash has not been able to independently verify it.
But Iran’s Atomic Energy Organization confirmed in a statement on Sunday that a hacker group had broken into a subsidiary’s network and had free access to its email system.
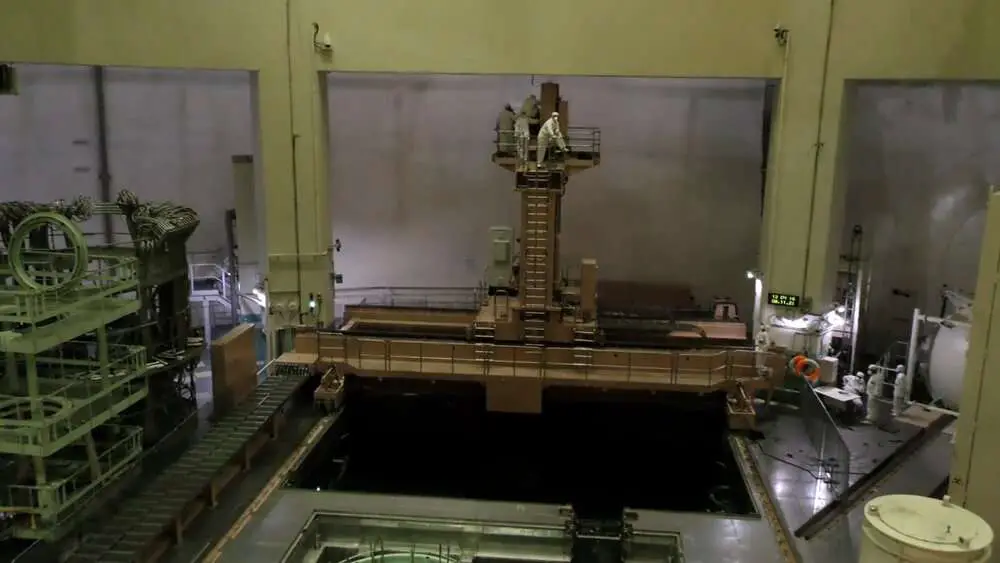
The organisation’s statement said that the emails contained “technical messages and routine and ongoing everyday exchanges.”
The hacker group has also released what it says are pay stubs for employees of the Iran Atomic Energy Production and Development Company along with visa and passport information of Russian and Iranian experts working at the Bushehr Nuclear Power Plant, on the Persian Gulf, in south-western Iran.
Work on the Bushehr Nuclear Power Plant started in 1975 under the orders of the Shah, Mohammad Reza Pahlavi, but was stopped in 1979 after the Islamic revolution.
The site was then bombed in the Iran-Iraq War (1980-1988) before Iran signed a 1995 deal to work with Russia at the site.
The plant eventually opened in 2011 during a ceremony that was attended by Russian Energy Minister Sergei Shmatko.
Russia and Iran agreed to build two new nuclear reactors at the site in 2014, with work beginning in 2017.
Protests have been gripping Iran after the death of Mahsa Amini, 22, from Saqqez, Kurdistan Province, who was on a visit to Tehran when she was arrested by morality police accused of violating hijab rules on 13th September.

She was allegedly beaten while in custody and spent the following days in a coma in the hospital before succumbing in the ICU on 16th September.
The clinic where she was treated said in a now-deleted social media post that she had been admitted brain-dead.
Alleged medical scans of her skull leaked by hackers showed that she had suffered bone fractures, haemorrhages, and brain oedema.
Anti-regime media are claiming that Mahsa’s medical records showing her history of heart disease were faked by the Iranian government.
The protests her death sparked are ongoing and, according to the non-profit Iran Human Rights, at least 201 people, including 28 children, have been killed so far, according to its latest figures released on 12th October.



